Compliance with regulatory frameworks is essential for organizations yet can often prove to be a complex challenge, especially for those utilizing Linux systems. Manual management of security controls can be time-consuming, diverting valuable resources away from strategic business initiatives. In this article, we will explore how UTMStack, an open-source Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) solution, simplifies compliance management specifically for Linux-based environments by automating assessments, continuous monitoring, and reporting.
Understanding Compliance Automation with UTMStack
UTMStack centralizes logs from various organizational systems, making it uniquely capable of dynamically assessing compliance controls. By continuously processing real-time data, UTMStack automates the evaluation of critical compliance facets such as encryption, two-factor authentication (2FA), and user activity. This level of automation vastly enhances the compliance landscape for Linux administrators.
Figure 1: Automated evaluation of compliance framework controls.
Example Compliance Control Evaluations
- Encryption Enforcement: UTMStack monitors logs to identify instances where encryption is critical, such as data in transit or at rest. It assesses compliance in real-time to ensure that protocols like TLS are enforced and alerts administrators upon potential non-compliance. For example, if a system receives a server certificate from an untrusted authority, automation would trigger an immediate alert.
- Two-Factor Authentication (2FA): Utilizing aggregated authentication logs, UTMStack checks for consistency in 2FA policy enforcement across the organization. Automated alerts are generated whenever deviations occur, allowing for timely remediation. For example, an Office365 authentication attempt logged with successful MFA usage would confirm 2FA compliance.
- User Activity Auditing: UTMStack continuously audits user and device activity through comprehensive log processing, identifying privileged account usage, abnormal access patterns, and potential compliance risks, enhancing the overall security posture in Linux systems.
No-Code Compliance Automation Builder
One of UTMStack’s standout features is its user-friendly, no-code compliance automation builder. Organizations can craft custom compliance assessments and workflows tailored to their specific regulatory obligations, without needing programming expertise. This empowers compliance teams to rapidly create intuitive frameworks capable of adapting to changing compliance needs.
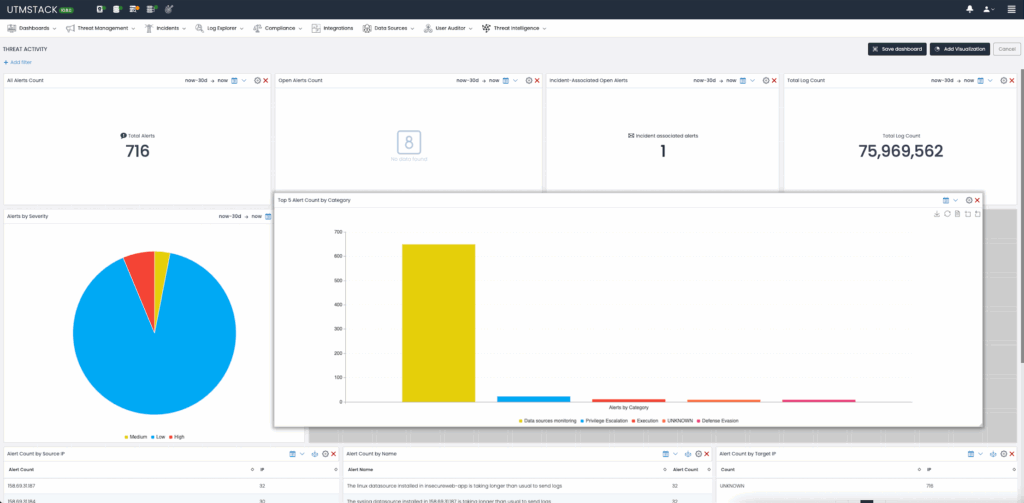
Figure 2: Compliance Framework Builder with drag-and-drop functionality.
Creating Custom Compliance Checks
With UTMStack’s no-code interface, users can:
- Define custom compliance control logic visually.
- Establish automated real-time monitoring of specific compliance conditions.
- Generate and schedule tailored compliance reports.
This significant reduction in administrative overhead allows compliance teams to focus on strategic initiatives, fostering a more proactive approach to regulatory demands.
Unified Compliance Management and Integration
Beyond automation, UTMStack acts as a centralized compliance dashboard where external compliance validations can also be manually declared. This unified view allows organizations to streamline their compliance audits seamlessly. The robust API capabilities of UTMStack facilitate integration with existing Governance, Risk, and Compliance (GRC) tools, enhancing overall compliance management.
Sample Use Case: CMMC Automation
In the context of CMMC compliance, organizations must demonstrate comprehensive data security and availability practices. UTMStack automates the evaluation of such controls, analyzing continuous logs, user access patterns, and firewall configurations. Automated reporting delivers clear documentation detailing compliance statuses, enabling organizations to proactively tackle any potential non-compliance issues.
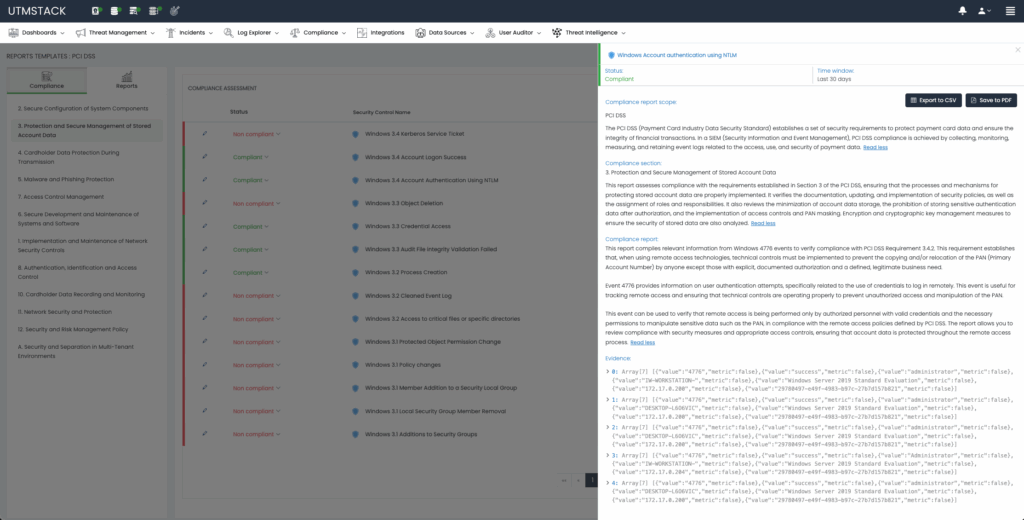
Figure 3: CMMC Compliance Control details.
Compliance Control Evidence Remediation
When controls are deemed compliant, UTMStack automatically collects evidence, including relevant logs to support documentation. If non-compliance is identified, AI-driven techniques provide remediation steps for security teams, streamlining the entire process of compliance management.
API-First Compliance Integration
With UTMStack’s API-first approach, organizations can seamlessly integrate compliance workflows into their existing IT ecosystems. This feature minimizes manual data handling, significantly enhancing compliance accuracy and efficiency—essential for any Linux administrator navigating regulatory challenges.
Summary
Managing compliance doesn’t have to be complex. UTMStack’s open-source SIEM and XDR solution streamlines compliance with standards like CMMC, HIPAA, PCI DSS, and GDPR for Linux environments. By automating assessments and monitoring while offering no-code customization, UTMStack alleviates the intricacies of compliance management.
Organizations can rapidly customize workflows and integrate seamlessly with their existing tools, making UTMStack invaluable for compliance and security teams striving for efficiency.
Join Our Community
UTMStack is constantly evolving, and we welcome contributions from the cybersecurity community to help shape the future of compliance automation.
FAQ
What is UTMStack?
UTMStack is an open-source Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) solution that automates compliance assessments and monitoring for various regulatory frameworks.
How does UTMStack benefit Linux users?
UTMStack simplifies compliance management for Linux users by automating evaluations and providing an intuitive no-code interface for custom compliance checks, thereby enhancing efficiency and reducing resource expenditure.
Can UTMStack integrate with existing compliance tools?
Yes, UTMStack offers robust API capabilities that allow seamless integration with existing Governance, Risk, and Compliance (GRC) tools for centralized compliance management.


