Explore the intricate world of shape-shifting phishing attacks and discover how modern cybercriminals use sophisticated tools to compromise security.

Phishing is a relentless threat in the cybersecurity landscape, evolved by cybercriminals seeking sensitive information such as login credentials. Among the tactics they employ, dynamically generated phishing pages have emerged as a major concern, leveraging tools like phishing-as-a-service (PhaaS) to create realistic login pages on demand.
These toolkits allow attackers, regardless of their technical skills, to produce and customize convincing phishing pages in real time. One notable example is the LogoKit, which first gained attention in 2021 and continues to pose significant threats as it adapts to changing security measures.
Understanding Dynamic Phishing Tactics
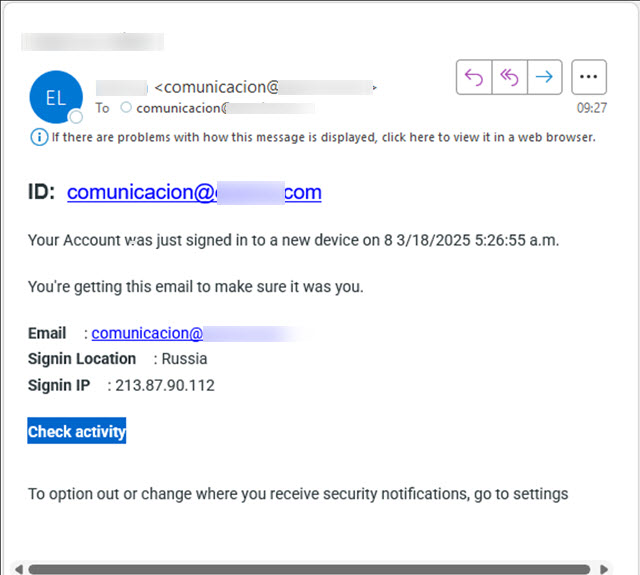
The process of these phishing attacks typically begins with an email designed to create urgency, potentially prompting you to click without thinking. This is the first step in a well-orchestrated scheme.
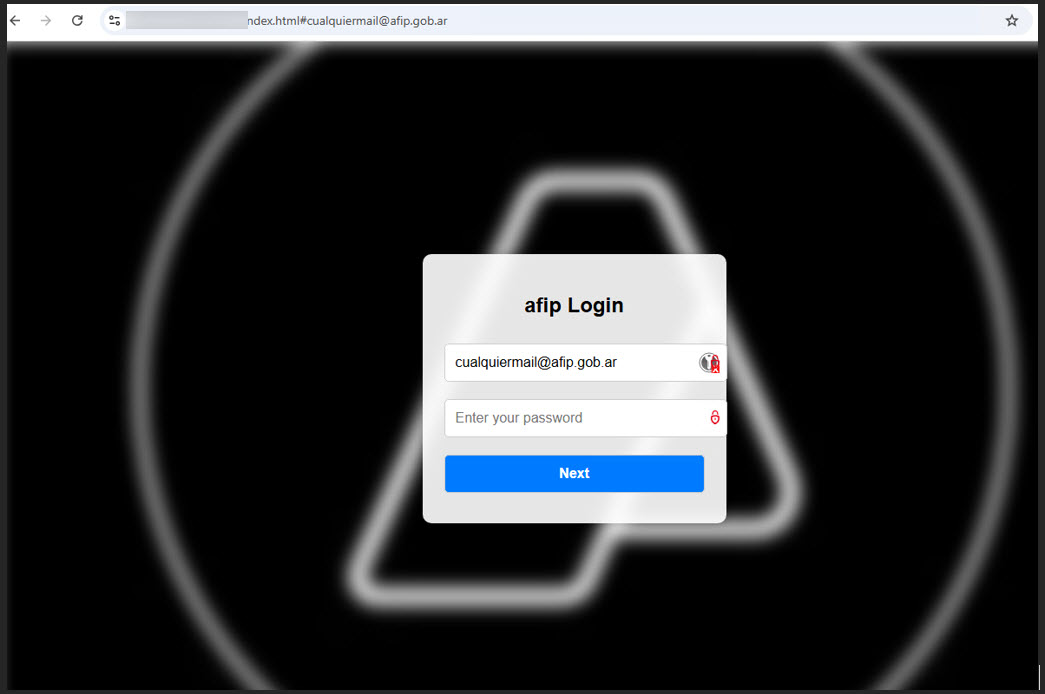
Clicking the link redirects you to a page that dynamically retrieves logos and branding elements of the impersonated company. This is made possible using APIs from legitimate marketing services, making the phishing pages appear incredibly authentic.
Furthermore, attackers may pre-fill your personal information, such as your name and email address, enhancing the illusion of legitimacy.
Why Cybercriminals Prefer Dynamic Phishing
The appeal of dynamically generated phishing lies in several key factors:
- Real-time customization: Attackers can swiftly alter a page’s appearance, sourcing logos on-demand.
- Enhanced evasion: Realistic visual elements help dodge detection by users and security filters.
- Scalable deployment: Lightweight infrastructure allows rapid scaling, making it difficult for defenders to identify threats.
- Low barriers to entry: Tools like LogoKit are easily accessible on underground forums, enabling non-tech-savvy individuals to launch attacks.
Protecting Yourself Against Phishing Attacks
Defending against phishing requires a blend of awareness and technical safeguards. Here are essential strategies:
Always verify any unexpected email or message that prompts you to click a link or share information. Navigate to trusted websites directly instead of clicking embedded links.
Use strong, unique passwords for all accounts, especially sensitive ones. Enabling two-factor authentication (2FA) is critical, providing an extra layer of security against unauthorized access.
Moreover, employ comprehensive, multi-layered security solutions with advanced anti-phishing features across all devices.
The Bottom Line
As cybercriminal tactics continue to evolve, so must our defenses. The dynamic nature of attacks like those using LogoKit demonstrates how readily available technology can be exploited for malicious purposes. Engaging in proactive security measures and maintaining vigilance are paramount in the battle against phishing threats.
FAQ
What is phishing-as-a-service (PhaaS)?
Phishing-as-a-service (PhaaS) refers to a business model where attackers provide tools and services to create phishing campaigns, making it easier for even non-technical individuals to launch attacks.
How can I identify phishing emails?
Look for suspicious email addresses, poor grammar, and urgent requests for information, along with unfamiliar links. Always verify the source before clicking any links or downloading attachments.
Is two-factor authentication really necessary?
Yes, two-factor authentication adds an essential layer of protection by requiring a second form of verification, making it significantly harder for attackers to access your accounts even if they steal your password.

